With the expansion of security considerations in the past decade and the increasing number of people designing technology, door-locking systems and security system coordination can be easily overlooked. This article will cover essential systems and mechanical and electronic locking technology. Additionally, it will explore the design concepts involving door hardware.
Mechanical Locks and Keys Basics
Mechanical locks secure doors as either deadbolts or door-handle devices. Keys serve as the means to unlock these mechanical locks, and possessing a working key determines who can access secured areas. Keys have cut grooves that match keyways to insert a key into the lock. The grooves are the first level of security; if they do not match, the key will not enter the lock. 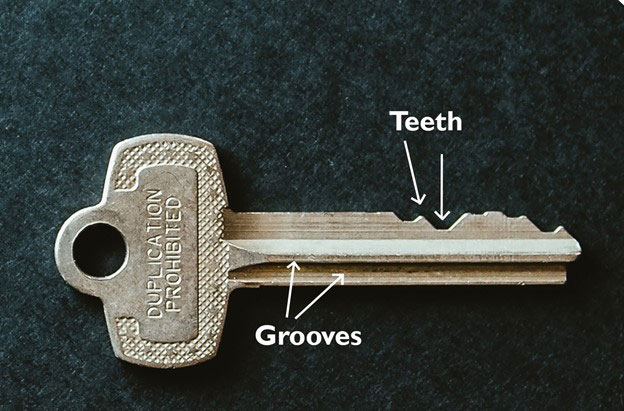
Next are the cuts, or “teeth,” on the key. These cuts correspond to the pins in a lock. They raise internal pins to an exact level to align them and allow a keyway to turn and activate a lock mechanism. If the key cuts do not match the pin size, the lock will not turn.
The level of security for a mechanical lock and key “system” can be improved by:
- Obtaining and reserving a restricted keyway (grooves) from the manufacturer. While not foolproof, it does help eliminate the easy duplication of keys by outside locksmiths.
- Standard keys are usually 5-pin keys; increasing the number to a 6 or 7-pin key system enhances the system’s security.
- Standard keys have a vertical pin and tumbler configuration. Higher security key systems utilize multiple angle cuts on the keys and in the pin and tumbler mechanism.
Master keys are keys that will open multiple locks. These keys function by adding wafers into the pin chambers to allow multiple depth cuts that align on the sheer line. The organization of a master key system can have several levels. Having a professional locksmith with experience in “master keying” set up a logical master key hierarchy is ideal. Master key systems can have many levels depending on the need, including:
- Single key
- Master key
- Grandmaster key
- Great-grandmaster key
Picking and Thwarting Locks
 “Lockpicking” is the process of opening a lock without a key, and it is not as easy as seen on TV. Lockpickers must have a keen tactile sense to get into the lock and raise each pin simultaneously to the sheer line, which is complicated and usually requires inserting a pick and tension bar. Adding the multiple-angle pin and tumbler, or specially shaped security pins to the configuration, adds to the complexity. However, newly developed lockpicking guns and other devices can assist in opening locks, which is a concern for security professionals. There are other less common methods, such as “bumping” that have become popular with less secure locks.
“Lockpicking” is the process of opening a lock without a key, and it is not as easy as seen on TV. Lockpickers must have a keen tactile sense to get into the lock and raise each pin simultaneously to the sheer line, which is complicated and usually requires inserting a pick and tension bar. Adding the multiple-angle pin and tumbler, or specially shaped security pins to the configuration, adds to the complexity. However, newly developed lockpicking guns and other devices can assist in opening locks, which is a concern for security professionals. There are other less common methods, such as “bumping” that have become popular with less secure locks.
Key Management
While lockpicking is a concern, most physical security breaches occur from lost, missing, or stolen keys. If a key is lost, a security expert should perform a risk assessment to determine vulnerability and whether the end-user should change the lock. Losing a key could be costly, especially if it is the master key.
Facility owners/occupants can take steps to help prevent losing keys, such as:
- Providing individuals with minimal-level key(s) needed to accomplish their work — do not issue master keys to everyone
- Securing/soldering key rings to prevent the removal of keys
- Adding an asset tracker to the key ring
- Holding key users accountable for returning all keys, especially master keys issued to contractors or outside vendors/consultants
- Integrating key boxes with security systems, including card readers that have identity management for key users, and setting up a notification system that will alert users of the key’s return time
Electronic Door Hardware
Electronic door hardware consists of devices that, when associated with either mechanical keys or electronic identity management systems, are a complete door management system.
Fail-Safe vs. Fail-Secure
Electronic door hardware includes two categories: power-to-secure or power-to-open. This is a significant distinction where fire and life safety codes apply. Life safety codes are designed to allow people to exit safely during a fire emergency.
- Fail-safe locks: Doors unlock when there is no power
- Fail-secure locks: Doors are locked when there is no power
In general, some designers universally apply fail-safe locks to ensure code compliance. However, fail-safe locks can become a security concern when a fire alarm activation or power failure occurs, allowing unauthorized access to vulnerable areas. A professional life safety and security consultant can design methods to provide a secure door and appropriate egress simultaneously. Typically, the best solution is a fail-secure electronic door hardware application with a mechanical means of egress.
Electrified Locksets/Strike
The most common electronic door hardware comes in electrified locksets or strikes. Electrified locksets require running power in the door, usually through a hinge to the door’s leading edge (door latch/knob side). In contrast, electrified strikes are mounted in the door frame and associated with mechanical hardware on the leading edge of a door. Both can be fail-safe or fail-secure. They also have an advantage in that they can be wired with low voltage power requirements, leading to power over ethernet (POE) options that can power the lock and connect it to the security network through a single cable.
Magnetic Locks
Magnetic locks, or “maglocks,” secure a door through an electromagnetic bond between the door frame and the door. It is typically a metal plate on the door with a magnetic device in the frame. These devices are strong and can effectively secure against brute force entry. However, they are fail-safe devices by design, and a power failure will eliminate their effectiveness.
There are also delayed-entry devices in the family of magnetic locks. These devices maintain security by preventing egress through the door for a short period (usually 15 or 30 seconds), which can help discourage a fleeing intruder from using the door to escape an area. These delayed-entry locks are often used in healthcare settings to delay child abduction or elopement cases.
Wireless Locks
The previously mentioned electronic door hardware devices are hard-wired for power. A newer concept is the wireless category of locks. These battery-powered locking devices are typically a lockset in the door. The battery life depends on use, but it can easily last more than one year before replacement. The locks have simple installation into new doors and can also be retrofitted for existing doors. All of the door control technology resides in a single piece of hardware.
Current life safety codes prohibit using these devices in areas where power must be dropped in a fire condition, as they lack wiring for power. Wireless locks can, however, be code compliant if used with a mechanical means of egress.
Door Design Impact on Operations and Maintenance
It is important to note the impact of door security design on those responsible for operations and maintenance. For example, a security integrator should be responsible for providing access controls and door hardware.
A security designer will provide the access control system design (card readers, communications, etc.) and the door hardware consultant will provide the door hardware in a schedule in design and construction projects; these are usually two different specification sections. The security designer and hardware consultant must coordinate closely, or the door(s) will likely have function issues.
A door hardware supplier typically provides the door hardware. This is because many doors do not have any security controls on them, and the security contractor does not want the responsibility for those doors. A best practice is to subcontract the door locksmith and hardware providers under the security integrator for doors with card readers. Having all three parties work together helps ensure that all components work together seamlessly and that they can quickly resolve any issues under one central point of contact, saving time and resources for the end user.
Summary
Security integrators should coordinate door hardware and security systems for optimal results. Proper planning and coordination in the design phase can prevent poor performance when the facility is in operation. And it helps to understand the basics of mechanical locks and electronic locks.
Remember that locks and electronics are but one layer of protection. Intrusion detection and video surveillance should be part of a holistic approach to security and safety. As always, a good, trusted advisor/consultant can help.
Lauris Freidenfelds is the vice president of Security Risk Consulting of Telgian Engineering & Consulting, LLC. His 40+ years of experience include operational security, technology, and emergency management programs. His knowledge of emergency management personnel and operations encompasses planning, organizing, and directing security programs and activities, as well as developing and coordinating disaster preparedness plans, the mitigation of, preparation for, and recovery from hazards and disasters. Lauris can be reached at [email protected].
The views expressed by guest bloggers and contributors are those of the authors and do not necessarily represent the views of, and should not be attributed to, Campus Safety.













